Can I tell if a keylogger has been installed on the machine I share?
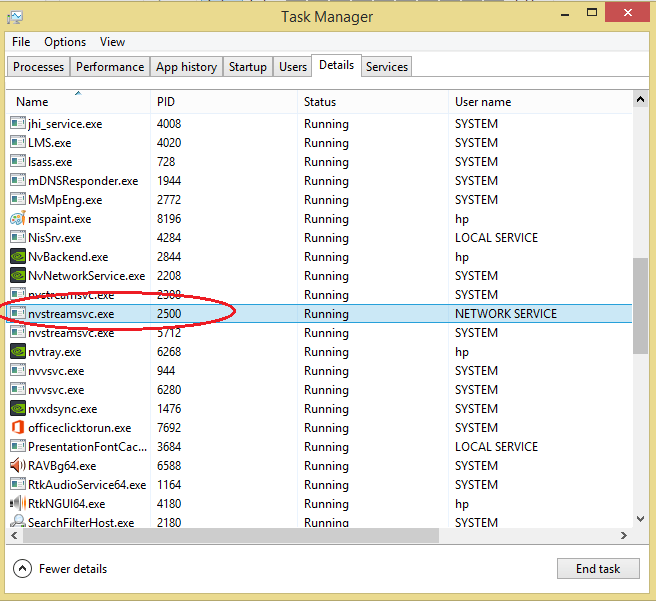
It prevents keyloggers from recording more keystrokes and transmitting the information to the hacker. That is how to detect keystroke logger in Task Manager. So how to detect keystroke logger in Programs and Features? You can ensure the protection of your computer from keyloggers by doing a full malware scan. The anti malware software will scan the hard drive folders to identify any malicious software hiding in the computer.
So how to do a full malware scan? That should have eliminated a keylogger from the computer. That is how to detect keystroke logger on the PC using anti malware software.
What is a keylogger and how does it work?
If you suspect that a keylogger is installed on your Android phone, go through your files and look for any suspicious folders in it. Any application installed on your phone creates a folder on your phone. If you believe that the folder is unimportant, you can delete it. Another way to detect keyloggers on Android is by checking the application manager.
Check the applications installed on your computer. If you download applications outside of the Google Play Store, the chances of you getting a keylogger infection are higher. Some APK apps are infected with malware. One security framework available to organizations struggling with on-premises and cloud access control issues is a As enterprise cloud adoption increases, the market for cloud identity governance is expected to expand.
- Learn to There Is a Surest Way to install Monitoring App on Android phone;
- Keylogger Removal?
- Subscribe to Help Desk Geek.?
Learn more about the use From understanding hardware components to managing network performance and security, this guide teaches networking newbies how to As network as a service gains traction, enterprises and service providers must consider multiple deployment models. Ansible, Terraform and Vagrant are common infrastructure automation platforms with specific use cases, benefits and drawbacks.
Social media algorithms, like those from Facebook, Twitter and YouTube, have created economies and sowed misinformation.
As organizations are adopting more agile practices, we're diving into how they can benefit from creating cross-functional agile Andi Karaboutis, group chief information and digital officer at National Grid, discusses the ways in which she's utilizing data The proprietary Apple silicon allows for an iPad Pro and an ultra-thin iMac with faster processing and graphics than previous Anywhere Workspace is an integrated product bundle that includes Workspace One, the VMware secure access service edge Zero trust is a complex term, but organizations that take security seriously must know what it is and how it can support existing The fight between AWS and Elastic over the commercial usage of Elasticsearch highlights how open source software vendors need to Here's a primer on how to calculate the total cost of a cloud migration and compare your on-premises expenses to what you'll Bans batter revenues at Huawei, which is bracing for more challenges but insists good times are ahead in 5G and comms software.
Study from Centre for Economics and Business predicts that ultrafast fibre-to-the-premises broadband could bring one million Challenges arising from the pandemic have left gaping holes in banking security, putting consumers at risk of fraud. Or even a home computer used by many family members? Well, all bets are off in that case. This makes a request to isolate xterm keystrokes from other x11 apps.
What is a Keylogger and How Can I Detect One on My Home Computer?
This doesn't prevent kernel loggers, but is just one level of protection. Yes, Ubuntu can have a key-logger. Its far fetched, but it can happen.
- The Best Android Monitoring Software;
- They aren’t always illegal.
- Related Posts?
It can be exploited via a browser and an attacker can run code with your user privileges. It can use auto-start services which run programs on login. Any program can get scan codes of pressed keys in X Window System. It is easily demonstrated with xinput command. See GUI isolation for more details. The only thing that you can do is check for rootkits.
Linux keyloggers can be made from languages that are compatible with the system and would require the use of local file storage to record this data and, if programmed to do so, if you do have a keylogger that was manually programmed or downloaded to work with this operating system then it may actually be a file, possibly renamed to look like a system file, anywhere on the system.
- Top Best New iPhone Hacking Camera App;
- Keyloggers: How they work and how to detect them (Part 1) | Securelist?
- The Tracking App for Spying on mobile phone.
If you do have a keylogger of this type, I'd attempt to find and remove it but if it is indeed something that was downloaded or installed I'd consider this highly unlikely as Linux is a secure operating system that is usually not suspect to forms of viruses you would normally find on Windows systems. Ubuntu Community Ask! Sign up to join this community.
How to check if your boss is monitoring your every keystroke
The best answers are voted up and rise to the top. Stack Overflow for Teams — Collaborate and share knowledge with a private group. Create a free Team What is Teams? Learn more. How can I detect a keylogger on my system? Ask Question.
